Endpoint Monitoring Software to Improve Cybersecurity
Our endpoint monitoring platform delivers real-time threat detection, data protection, and workforce insights while preventing insider threats and data loss across all your endpoints.

How Teramind Makes Endpoint Monitoring Easy
Real-Time Threat Detection
Identify suspicious activity and anomalous user behavior instantly with behavioral analytics that establish baselines and flag deviations that could indicate security risks.
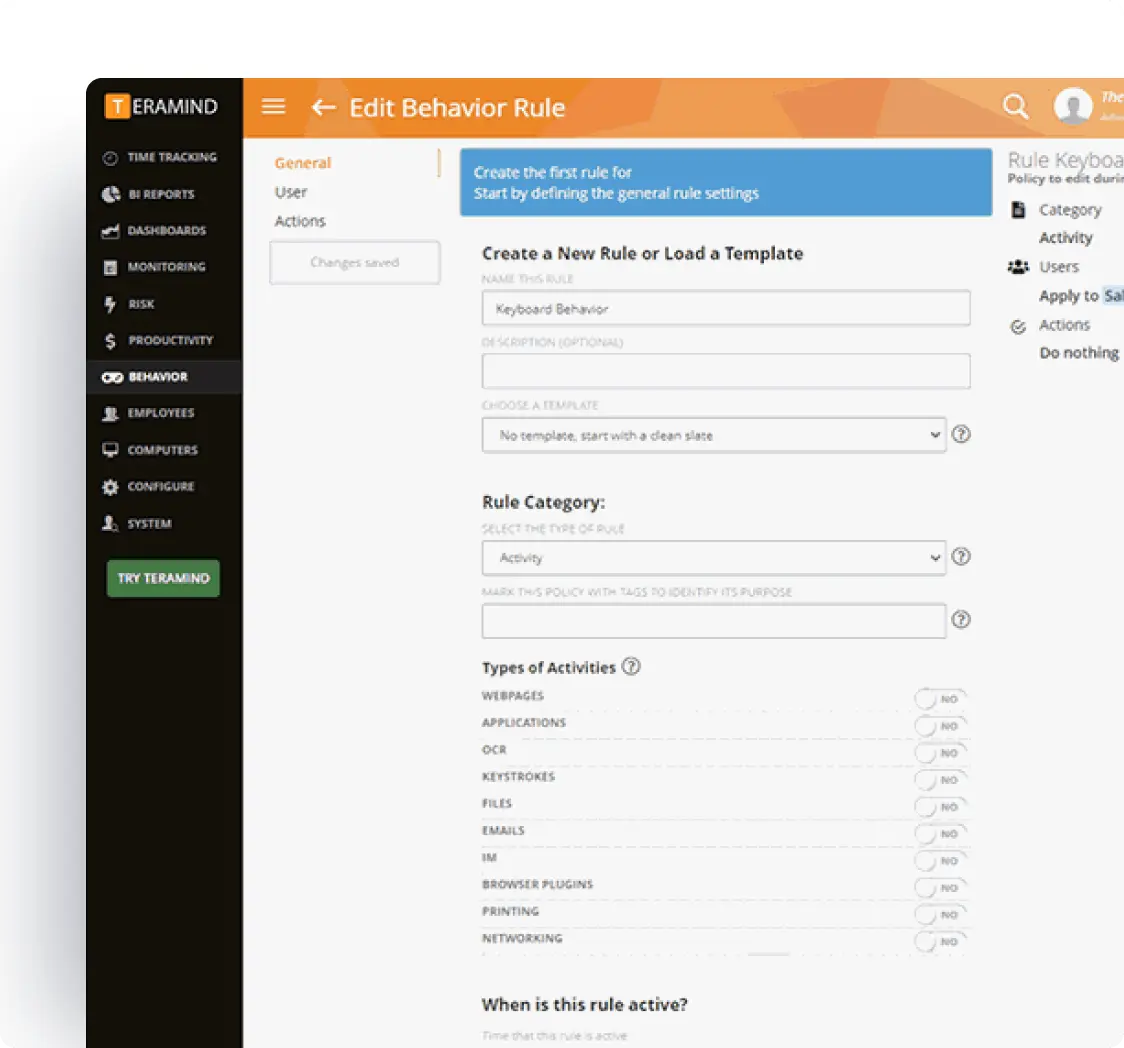
Granular Control
Manage all endpoints from one platform with our unified endpoint management system that provides complete visibility across your IT estate.
Comprehensive Visibility
Monitor all user activities across endpoints with screen recordings, automated responses, and detailed reporting that provide complete context for every action. Support users during remote work while maintaining security measures across your entire network of devices.
Teramind’s Endpoint Monitoring Tools
Protect your organization’s most valuable assets with our advanced endpoint management software capabilities. Our endpoint management solution provides the tools security teams need to secure your digital infrastructure and identify potential insider threats.
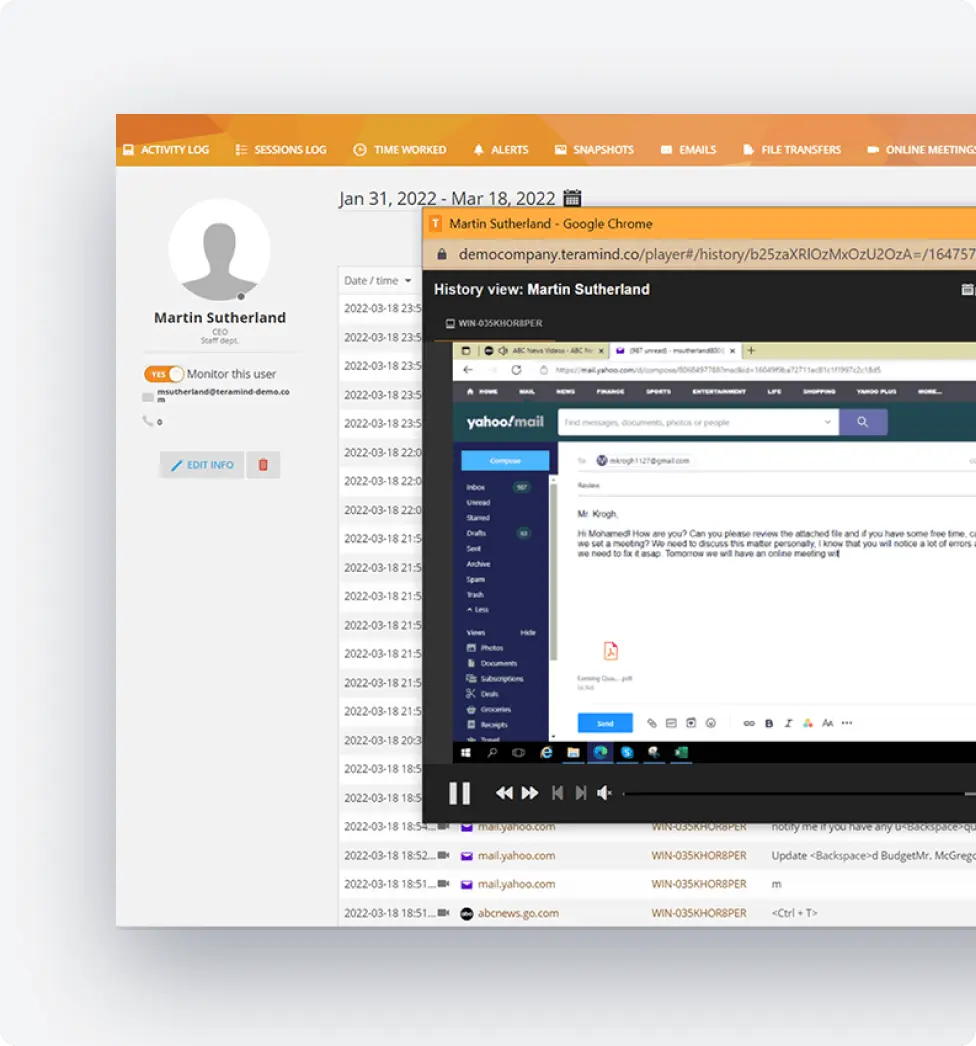
Employee Activity Monitoring
Track all employee actions on endpoints for complete visibility when investigating suspicious activity or productivity concerns. Our endpoint monitoring software records everything happening on your network.
-
Full session recordings with video playback for forensic investigations
-
Detailed keystroke tracking to identify suspicious patterns across all devices
-
Application usage monitoring with configuration management capabilities
-
Comprehensive website tracking to control access and prevent data loss
Threat Detection and Response
Leverage machine learning to establish baseline behavior patterns and detect anomalies that could indicate cyber threats. Our endpoint management software uses advanced analytics not found in standard endpoint management solutions.
-
Automatic risk scoring of employee actions based on potential threat level
-
Predictive analytics to identify potential threats before incidents occur
-
Real-time monitoring alerts on suspicious activity via our unified dashboard
-
Deep visibility into unusual data access or handling patterns across all monitored endpoints
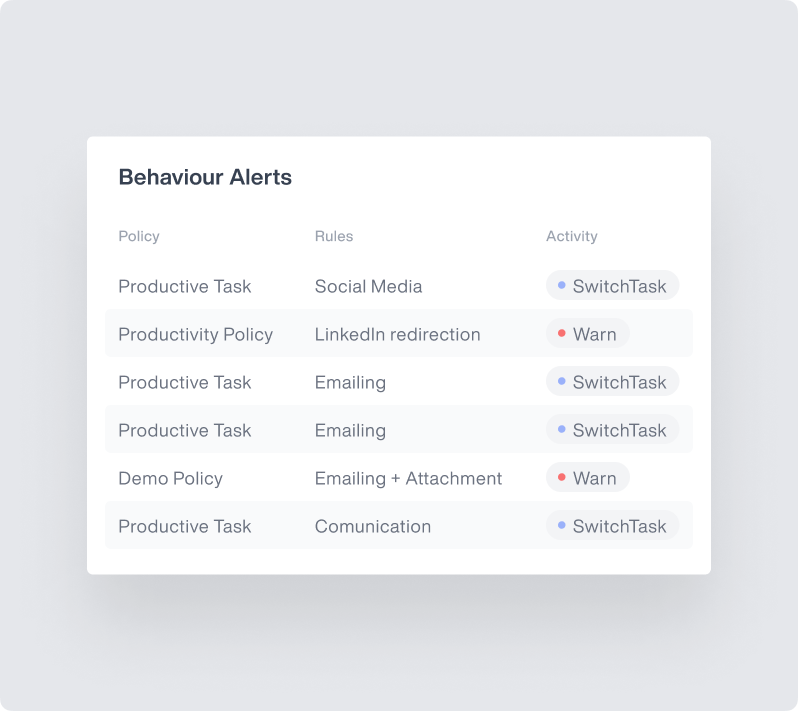
Behavioral Data Loss Prevention
Prevent sensitive data exfiltration with content-aware monitoring and automated responses to policy violations.
-
File monitoring with forensic analysis to prevent data loss
-
Email and communication channel monitoring to detect unauthorized sharing
-
USB and removable media controls to manage access to sensitive data
-
Content discovery to identify and protect critical business assets
Advanced Forensic Investigation
Conduct thorough investigations of security incidents with comprehensive audit trails and forensic tools.
- Full video recording playback of user sessions for detailed forensic analysis
- Historical activity logs to reconstruct incident timelines
- Detailed audit trails to support compliance and security investigations
- Export capabilities for evidence preservation and reporting to security teams
Remote Access Management
Secure management of remote endpoints to support users working from anywhere while maintaining security.
-
Remote control capabilities for instant troubleshooting
-
Secure access protocols for managed devices
-
Monitoring for remote work productivity and security compliance
-
Detection of unauthorized remote access attempts to prevent insider threats
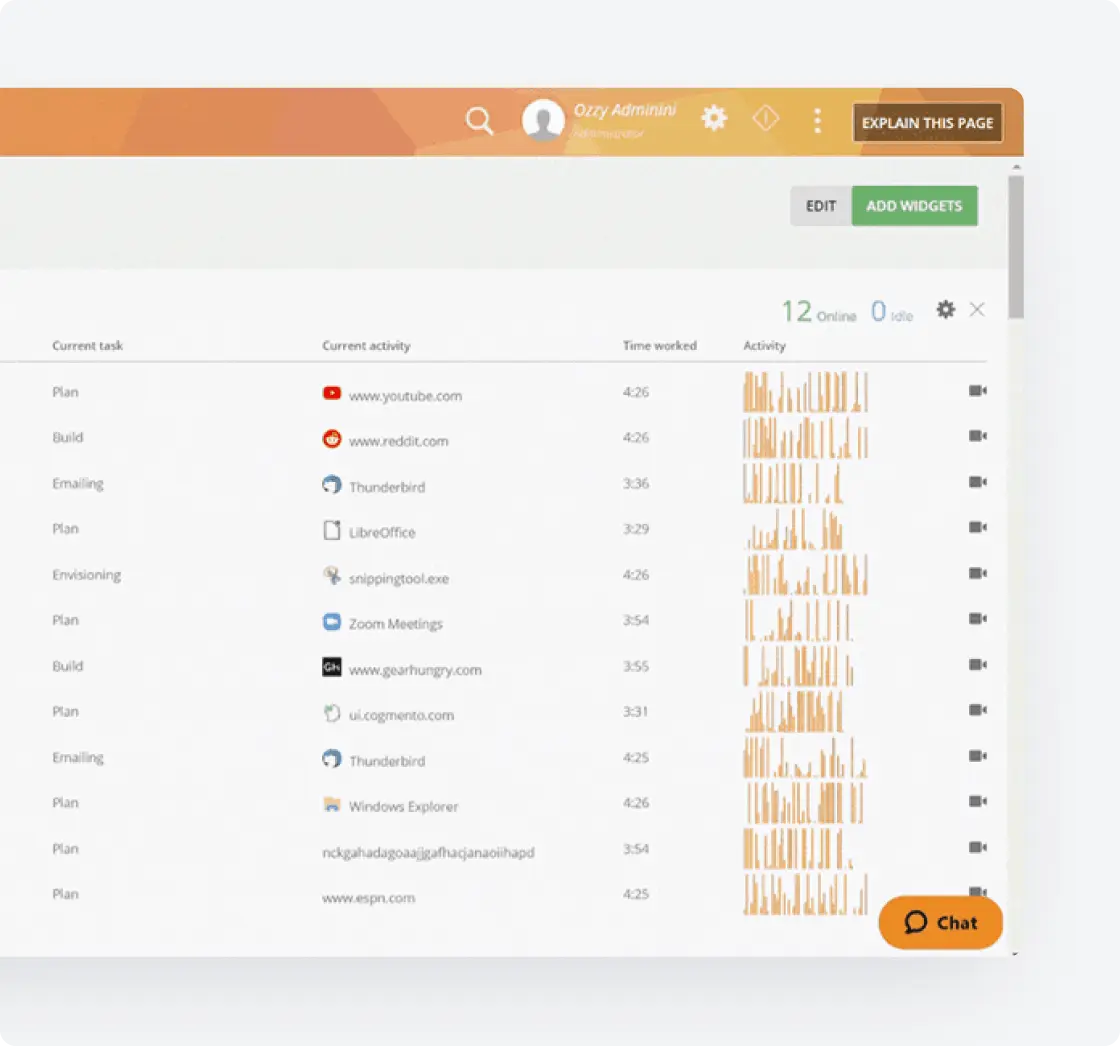
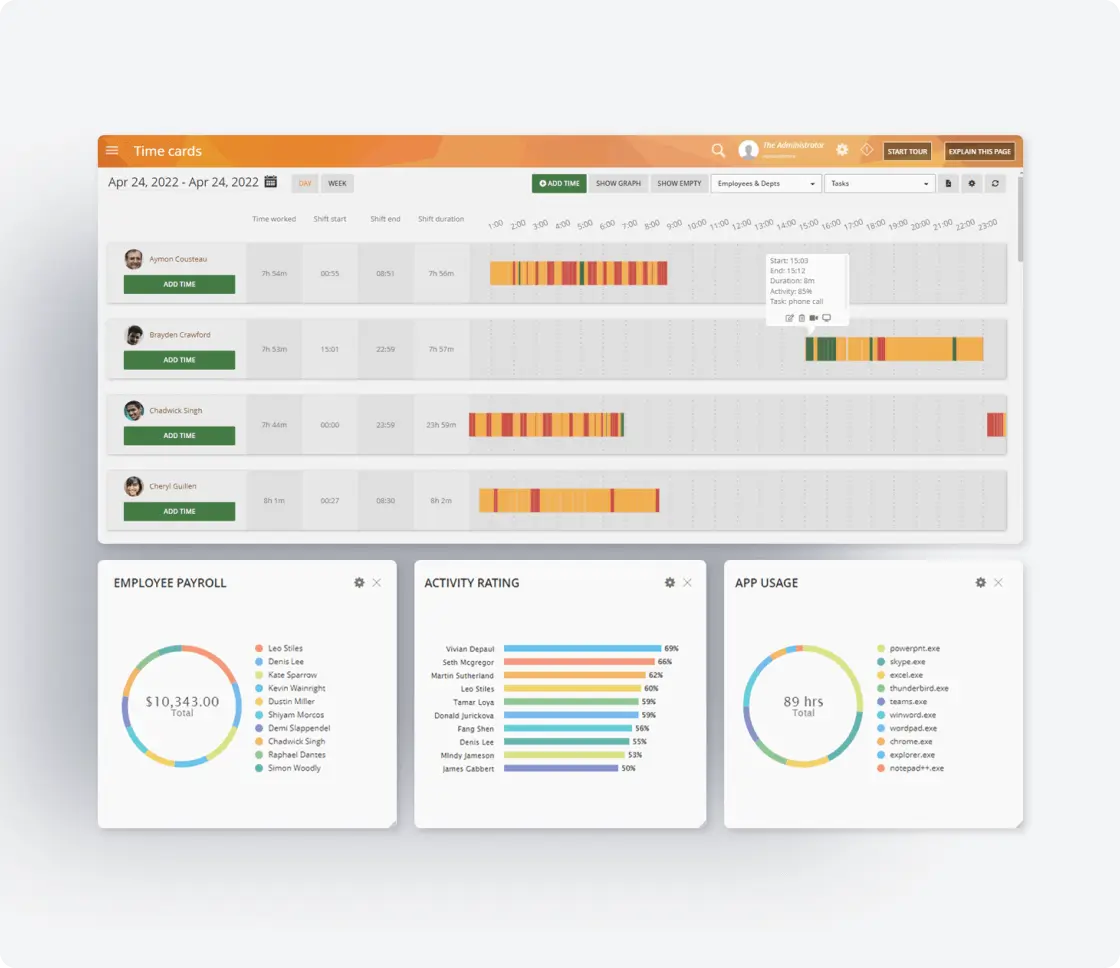
Productivity Monitoring
Optimize workforce efficiency with detailed insights into user activities and work processes.
-
Active vs. idle time tracking to measure true productivity on all endpoint devices
-
Application and website categorization as productive or unproductive
-
Identification of top performer work patterns to establish business process benchmarks
-
Automated time tracking and project reporting for comprehensive visibility
-
Detection of time falsification attempts that other management software might miss
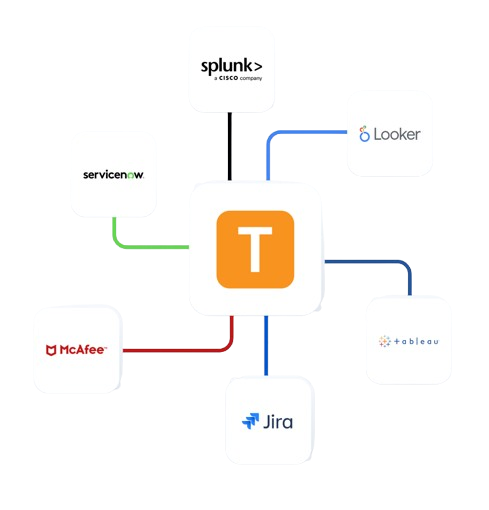
Enterprise Integrations
Integrate Teramind with your existing infrastructure to enhance security operations.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind’s Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What is endpoint monitoring software?
Endpoint monitoring software is a comprehensive security and productivity solution that tracks and analyzes user behavior on endpoint devices such as laptops, desktops, servers, and mobile devices. Teramind’s endpoint monitoring software provides real-time visibility into all user activities, allowing organizations to detect insider threats, prevent data loss, ensure compliance with security policies, and optimize workforce productivity. Unlike basic endpoint management software, our solution offers complete visibility into user activities with advanced threat detection capabilities that help maintain your organization’s security posture against persistent threats.
What is the best endpoint management software?
The best endpoint management software combines robust security features with productivity insights while respecting user privacy. Teramind consistently ranks as a leading unified endpoint management solution due to our comprehensive feature set that includes real-time monitoring, behavioral analytics for threat detection, content-aware data loss prevention, and detailed productivity analysis. Our flexible deployment options, intuitive centralized platform, and customizable security policies make Teramind the preferred choice for organizations seeking complete visibility into their IT estate without compromising efficiency.
What is endpoint detection software?
Endpoint detection software monitors and analyzes user behavior on devices to identify security threats and policy violations. Teramind’s endpoint detection capabilities go beyond traditional solutions by combining behavioral analytics with screen recordings, keystroke monitoring, and application tracking to provide complete context for suspicious activity. Our endpoint monitoring software not only helps detect cyber threats but also enables automated responses to block malicious actions before data breaches occur, making it a proactive first line of defense rather than just a detection mechanism. The comprehensive monitoring capabilities of our solution provide security teams with unmatched visibility into potential insider threats and vulnerabilities across your entire network infrastructure.
What software do you use for endpoint management?
Organizations across industries choose Teramind for comprehensive endpoint management because our software delivers the perfect balance of security, compliance, and productivity features. Teramind’s endpoint monitoring solution provides unmatched visibility into user activities with features like screen recording, application monitoring, website tracking, and control of remote access. Our behavioral analytics engine establishes baselines of normal behavior and alerts you to anomalies that could indicate insider threats or data loss attempts, while our productivity tracking helps optimize business processes and identify efficiency improvements. When searching for endpoint management software, security-conscious organizations consistently select Teramind’s integrated solution for its powerful capabilities in managing all endpoints through one centralized platform.
The post Endpoint Monitoring Software first appeared on Teramind.
Source: itsecuritycentral.teramind.co

